Security, Safety and Protection are things that we will always struggle with, no matter who you are, regardless of the kind of house you live in, or where you live – security will always be a concern.
Security Threats can find you anywhere, at any time and everyone is vulnerable. We blindly look to technology, believing its efficient and all we need to protect us, but as much as that is true, the equivalent [if not more] works in favour of the same threats we need protection from.
Crime evolves with technology. It equips criminals with better, more efficient tools and creative ways to carry out their crimes. No surprise there!
We no longer have the luxury of concerning ourselves with just home and body safety – there is a big dark cyber world out there, and their attacks are more severe and lasting than any home burglary. And with today’s social media obsession, who’s really to blame? We put ourselves out there, documenting every detail of our lives for anyone and everyone to see, risking personal information/details that you think is safe, but easily accessible to those who know where and what to look for!
Fact: South Africans spend an average of 8 hours online per day, a third of which is on social media.
Point: Protecting yourself online is important, more than you might think.
One of the many threats out there is Identity Theft.
It is real and serious and it’s an ever growing and terrifying danger that you have to protect yourself from.
It is easy to laugh off and think, this will never happen to me, but just one wrong click on the internet, or 1 fake telesales call where you are distracted and divulge some personal info you should not have and WHAM – that comfortable ‘I would never be so stupid’ rug is swept from under your feet and before you even comprehend what just happened, it’s gone… its all gone – your life, your money, your credit, your Identity!
Ever lose your wallet, or had it stolen? I have.
It’s a massive pain and so inconvenient and time-consuming, having to run around and cancel cards, get new cards, replace your ID or Drivers license [which means hours at home affairs] and of course, let’s not forget – buying a new wallet!.
Now, think what its like when your whole life is stolen, your identity – which is all you have that is actually yours, something that no one is supposed to ever be able to take from you – but they do, they have, and they will continue to do so – and anyone can be next.
Losing a wallet or having it stolen is unpleasant, disruptive and inconvenient.
Having your personal info/identity stolen/hacked is, without measure, WAY worse
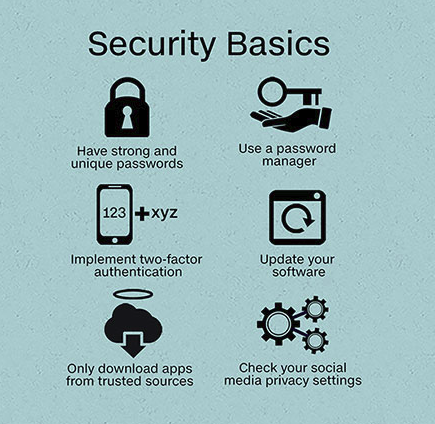
So today I am sharing 5 Basic security tips [thats not as basic as it sounds because so many don’t think of it] to protect you from Identity theft:
1. Keep your Tax Info, Bank Statements, and financial docs in a secure place.
2. NEVER EVER give anyone your ID number or any other personal information unless you initiated the contact or you are sure that you know who you are dealing with
3. Your cellphone is not safe! NEVER EVER save sensitive information such as ID Numbers, Bank Login Details or PINS etc on your mobile.
Fingerprint and password-protected phones are never full proof – there’s always a way around it to unlock the phone.
If your phone is stolen with sensitive information stored on it, you have literally handed your identity to criminals all wrapped up with a pretty bow on top – to do with as they see [pro]fit!
4. Tighten up on your social networking security settings. It is known that Criminals can make use of the information obtained on social media platforms,
And do not ever respond to emails that provide you with a website link which requires you to either log in with a password, or update personal information
5. Protect your computer/phone/laptop from hackers by keeping your software up to date, install security apps and keep them up to date to help keep your devices more resilient against automated hacking tools.
Create complex Passwords on everything, and change them regularly. And do not save said passwords anywhere on any of your devices either!
It can never be emphasized enough: Always Protect your Personal and Financial Information.
Sources:
Businesstech
SARS
Kaspersky
CreativeBloq
Locklatch
TomsGuide
If you are interested in becoming one of our subscribers, please visit Leads 2 Business.
To view notes with screenshots on how to use our website, please visit Leads 2 Business Wiki.
To view more Articles, please visit our Leads 2 Business Blog.
My epic journey at Leads 2 Business started September 2008, as a Researcher / Data Capturer in the Tenders Africa Department.
I joined Customer Relations in 2011, where I have had the great pleasure of being part of the Dynamic L2B Admin Department [From 2011 to present].
I deal with the Registration and Administration details of New Account Activations, and Existing Account Upgrades, etc. I also assist with client & staff queries.
I’m a ‘think-out-of-the-box’ individual and an excellent problem solver. I am hardworking, meticulous, efficient, friendly and always happy to help!
I look forward in assisting you with any queries you might have